The Future of Code Security: Insights on AI Transformation (feat. Nir Valtman)
AI is transforming software development by massively increasing code output, making context-aware security and quality controls essential rather than optional.
In this conversation, Nir Valtman, co-founder and CEO of Arnica, discusses the transformative impact of AI on code security and the software development lifecycle. He emphasizes the importance of understanding vulnerabilities, managing dependencies, and integrating security into developer workflows. In a rapidly evolving digital landscape, ensuring code security has never been more critical.
Krish & Nir dive deep into the transformative role of artificial intelligence in software development life cycles. Nir shares his unique insights on how AI is reshaping code security and the essential steps developers must take to mitigate risks. The discussion also touches on the balance between feature development and security, the role of AI in generating code, and the evolving landscape of development teams.
Podcast
Building Secure Software in an AI-First Development World - on Apple and Spotify.
Understanding the Landscape of Code Vulnerabilities
In today’s software development environment, vulnerabilities can emerge from various sources, including outdated libraries and complex dependency trees. Nir highlights the significance of understanding not just the vulnerabilities themselves but their exploitability context. For example, he discusses well-known vulnerabilities such as Log4j and recent software supply chain attacks, emphasizing that recognizing a vulnerability is only the first step. Developers must assess whether the vulnerable code is actually used in their application, which is termed “reachability analysis.”
The Importance of Reachability Analysis
Nir explains that reachability analysis allows developers to determine whether a vulnerable function is actively utilized in the source code. This critical step helps prioritize which vulnerabilities to address first, as not all vulnerabilities pose the same level of risk. For instance, a developer might find that an outdated package has several vulnerabilities, but through reachability analysis, they can pinpoint that only a fraction of those vulnerabilities are relevant to their application. This targeted approach not only saves time but also enhances the overall security posture of the application.
Building a Robust Dependency Tree
One of the biggest challenges developers face is managing the intricate web of dependencies that modern applications rely on. Nir discusses how Arnica’s platform helps by rebuilding the entire dependency tree of a project, identifying direct and transitive dependencies, and assessing the impact of potential upgrades. This level of scrutiny is essential, especially when considering that upgrading a package can lead to breaking changes across the codebase. By providing a clear view of these dependencies, developers can make informed decisions about upgrades and patches.
Leveraging AI for Enhanced Security
As Nir points out, the integration of AI in security processes is becoming increasingly important. AI can analyze changelogs, code diffs, and even predict potential breaking changes. However, he acknowledges that while AI can assist in these areas, it is not foolproof. Developers must still exercise caution and conduct thorough assessments before implementing changes, as the complexity of dependency trees can lead to unforeseen issues.
Balancing Feature Development and Security
A common dilemma faced by many organizations is the conflict between addressing vulnerabilities and focusing on feature development. Nir candidly discusses this tension, noting that while security is paramount, the drive to innovate and expand product offerings can sometimes overshadow immediate security concerns. He stresses the importance of finding a balance, emphasizing that neglecting vulnerabilities can lead to severe consequences, including breaches that may compromise the entire system.
Rethinking Vulnerabilities: Context Over Volume
Modern development teams are overwhelmed by vulnerability alerts. According to Nir, finding vulnerabilities is not the hard part anymore—understanding which ones actually matter is.
Traditional scanners often flag issues without answering critical questions:
Is the vulnerable code actually reachable?
Is the vulnerable function used in production paths?
Would fixing it introduce breaking changes?
Arnica’s approach emphasizes reachability analysis—prioritizing only vulnerabilities that are demonstrably exploitable in a given codebase. Just as important, Nir stressed that declaring something “not reachable” carries real responsibility and must be done conservatively to maintain developer trust.
Dependency Management and the Reality of Breaking Changes
Upgrading dependencies sounds simple in theory, but in practice it’s risky. A single version bump can cascade across a complex dependency tree, especially with transitive dependencies. Nir highlighted that:
Developers often settle for “partial wins” (patch or minor upgrades) rather than risky major upgrades.
There is no reliable, deterministic way to predict breaking changes across large dependency graphs.
AI can assist by analyzing changelogs and diffs, but human judgment remains essential.
Security vs. Feature Delivery: A False Tradeoff
One recurring tension in software teams is whether security work slows down feature development. Nir challenged this assumption.
Research cited in the conversation shows:
Developers spend ~15% of their time in code reviews.
Roughly 63% of AI-generated review comments are dismissed as noise.
A significant portion of developer time is wasted evaluating low-value findings.
By reducing noise and surfacing only actionable, contextual issues earlier in the workflow, teams can actually increase overall feature velocity, not reduce it. Nir estimates that well-designed security workflows can result in more features shipped, not fewer.
Tribal Knowledge and Personalized Security
One of the most forward-looking ideas from the conversation was tribal knowledge. Over time, tools can learn:
Which issues teams routinely dismiss
Which patterns reflect real business logic
Where a specific team’s blind spots lie
By feeding this context back into scanning and AI generation, security tooling becomes increasingly personalized and aligned with how each team actually builds software, rather than relying on generic rulesets.
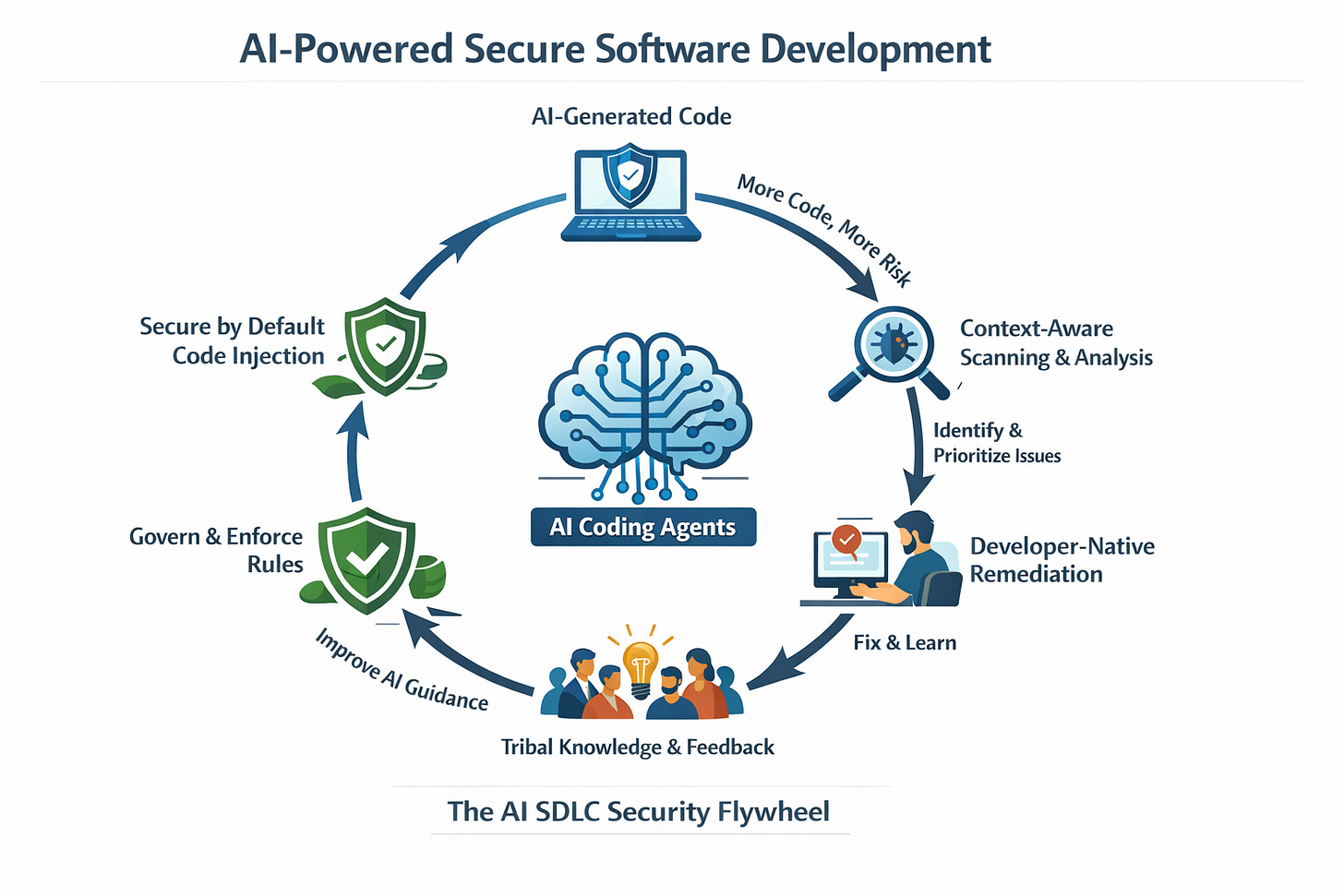
AI’s Impact on the SDLC: More Code, More Risk
Looking ahead, Nir cited predictions that up to 90% of new code may soon be AI-generated. This creates three major challenges:
Exploding risk surface – more code means more potential vulnerabilities.
Ownership ambiguity – AI-generated code often lacks clear authorship.
Review bottlenecks – human review capacity doesn’t scale linearly.
The solution, he argued, lies in creating a feedback loop—or “flywheel”—where organizational knowledge about risks, dismissals, and fixes continuously informs how AI generates future code.
AI Coding Agents and “Secure by Default” Development
As AI coding assistants become ubiquitous, a new problem emerges: fragmented behavior across tools like Copilot, Cursor, and Claude. Each may follow different rules—or none at all.
Nir described a model where organizations centrally define AI coding rules (security, quality, governance) and automatically inject them into repositories. Instead of relying on optional plugins or ignored pull requests, these rules become part of the codebase itself, ensuring that AI agents generate governed code by default.
Conclusion: Key Takeaways for Developers
As software development continues to evolve, so too must the strategies we employ to ensure security. Nir Valtman’s insights underscore the necessity of understanding the nuances of vulnerabilities, employing reachability analysis, and leveraging AI to enhance security measures. Developers must maintain a delicate balance between innovation and security, recognizing that the cost of neglecting vulnerabilities can far outweigh the investment in proactive security measures.